Top Healthcare Cybersecurity Best Practices for Providers

Healthcare providers are facing a digital onslaught like never before. Cyberattacks on hospitals doubled in the past five years and over 45 million patient records were exposed in 2023 alone. You might assume the real danger comes from complex hacking tools or ingenious malware. But the most common weak spot is much more ordinary—simple human error, like a missed email or a weak password, is often all it takes to jeopardize patient safety and privacy.
Table of Contents
- Understanding Healthcare Cybersecurity Challenges
- Key Cybersecurity Best Practices for Healthcare
- Building a Strong Security Culture in Healthcare Teams
- Meeting Compliance and Legal Requirements in Healthcare
Quick Summary
| Takeaway | Explanation |
|---|---|
| Conduct Regular Risk Assessments | Continual evaluation of vulnerabilities is essential to protect patient data and healthcare operations. Regular assessments enable early identification of potential weaknesses. |
| Invest in Cybersecurity Training | Comprehensive training programs for staff reduce human errors and enhance awareness against cyber threats like phishing. Employees must understand security protocols and their importance. |
| Implement Advanced Security Measures | Use multi-factor authentication, encryption, and continuous monitoring to safeguard sensitive health information from unauthorized access and breaches. |
| Foster a Security Culture | Leadership must advocate for cybersecurity, integrating awareness into daily practices to ensure all staff prioritize data protection effectively. |
| Ensure Compliance with Regulations | Maintain adherence to HIPAA and other regulatory standards to safeguard electronic protected health information and build trust within the community. |
Understanding Healthcare Cybersecurity Challenges
Healthcare organizations face unprecedented cybersecurity challenges that threaten patient safety, operational integrity, and institutional trust. The digital transformation of healthcare has exponentially increased vulnerability to sophisticated cyber threats, creating a complex landscape of technological and human risk factors.
The Escalating Threat Landscape
Cybersecurity best practices are now mission-critical for healthcare providers. According to the U.S. Government Accountability Office, healthcare systems confront a multifaceted array of cybersecurity risks that extend far beyond traditional IT security concerns. These risks include interconnected medical devices, outdated information systems, and persistent workforce cybersecurity awareness gaps.
The complexity of healthcare IT environments makes them particularly vulnerable. Medical networks integrate numerous devices and systems with varying security protocols, creating potential entry points for malicious actors. Electronic health records contain extremely sensitive personal information, making them prime targets for cybercriminals seeking financial gain or unauthorized data access.
Regulatory and Operational Challenges
Healthcare cybersecurity isn’t just about technology protection but also regulatory compliance and patient safety. Research published in Cureus highlights that cyber incidents can directly impact patient care delivery, potentially compromising treatment protocols and patient outcomes.
Key challenges include:
- Device Complexity: Hundreds of networked medical devices with varied security capabilities
- Data Sensitivity: Electronic health records containing comprehensive personal medical information
- Workforce Limitations: Insufficient cybersecurity training and awareness among healthcare professionals
Human Factor and Technological Vulnerabilities
The human element remains the most significant cybersecurity vulnerability. Healthcare professionals often lack comprehensive cybersecurity training, making social engineering attacks and phishing attempts particularly effective. Workforce education becomes as crucial as technological safeguards in preventing potential breaches.
Moreover, the healthcare sector’s critical nature means that cyber incidents can have immediate and potentially life-threatening consequences. Ransomware attacks can disable critical systems, interrupt patient care, and compromise emergency response capabilities. Understanding these multidimensional challenges is the first step toward developing robust, comprehensive healthcare cybersecurity strategies that protect both technological infrastructure and patient well-being.
Key Cybersecurity Best Practices for Healthcare
Healthcare organizations must adopt comprehensive cybersecurity strategies that protect patient data, maintain operational integrity, and ensure regulatory compliance. Implementing robust security practices is no longer optional but a critical necessity in an increasingly digital and threat-prone healthcare environment.
Comprehensive Risk Assessment and Management
Proactive security strategies require systematic risk evaluation and continuous monitoring. According to research published in Healthc Manage Forum, successful cybersecurity implementation demands collaboration between information technology, clinical, and administrative leadership. Organizations must conduct regular vulnerability assessments, identifying potential weaknesses across technological infrastructure, network systems, and human interactions.
Key risk assessment components include:
- Network Architecture Review: Comprehensive mapping of all connected devices and potential entry points
- Data Flow Mapping: Understanding how patient information moves through organizational systems
- Threat Modeling: Identifying potential cyber attack scenarios and their potential impacts
Advanced Technical Safeguards
Technical protection measures form the backbone of healthcare cybersecurity defense. The Biden administration’s proposed cybersecurity regulations emphasize the critical importance of robust encryption and data protection protocols. Healthcare providers must implement multi-layered security approaches that include:
To help readers quickly compare different technical safeguards recommended for healthcare cybersecurity, the following table summarizes key measures and their primary security benefits.
| Technical Safeguard | Description | Main Benefit |
|---|---|---|
| Advanced Encryption | Protects data at rest and in transit | Prevents unauthorized data access |
| Multi-Factor Authentication | Requires multiple forms of verification | Restricts unauthorized access |
| Continuous Monitoring Systems | Real-time threat detection and response capabilities | Enables immediate threat response |
| Regular Software Updates | Patches vulnerabilities in technological platforms | Closes security gaps |
- Advanced Encryption: Protecting patient data at rest and in transit
- Multi-Factor Authentication: Restricting unauthorized system access
- Continuous Monitoring Systems: Real-time threat detection and immediate response capabilities
- Regular Software Updates: Patching vulnerabilities across all technological platforms
Workforce Cybersecurity Education
Human factors remain the most significant cybersecurity vulnerability. Comprehensive workforce training programs are essential in creating a culture of security awareness. Healthcare professionals must understand their role in protecting sensitive patient information, recognizing potential security threats, and following established protocols.
Effective cybersecurity education should include:
- Phishing Awareness Training: Teaching employees to identify and report suspicious communications
- Password Management Protocols: Implementing strong password creation and management strategies
- Incident Response Preparation: Ensuring staff know immediate steps during potential security breaches
By integrating technical safeguards, continuous risk assessment, and robust workforce education, healthcare organizations can develop a holistic approach to cybersecurity. This comprehensive strategy not only protects sensitive patient data but also maintains the trust and reliability critical to effective healthcare delivery.
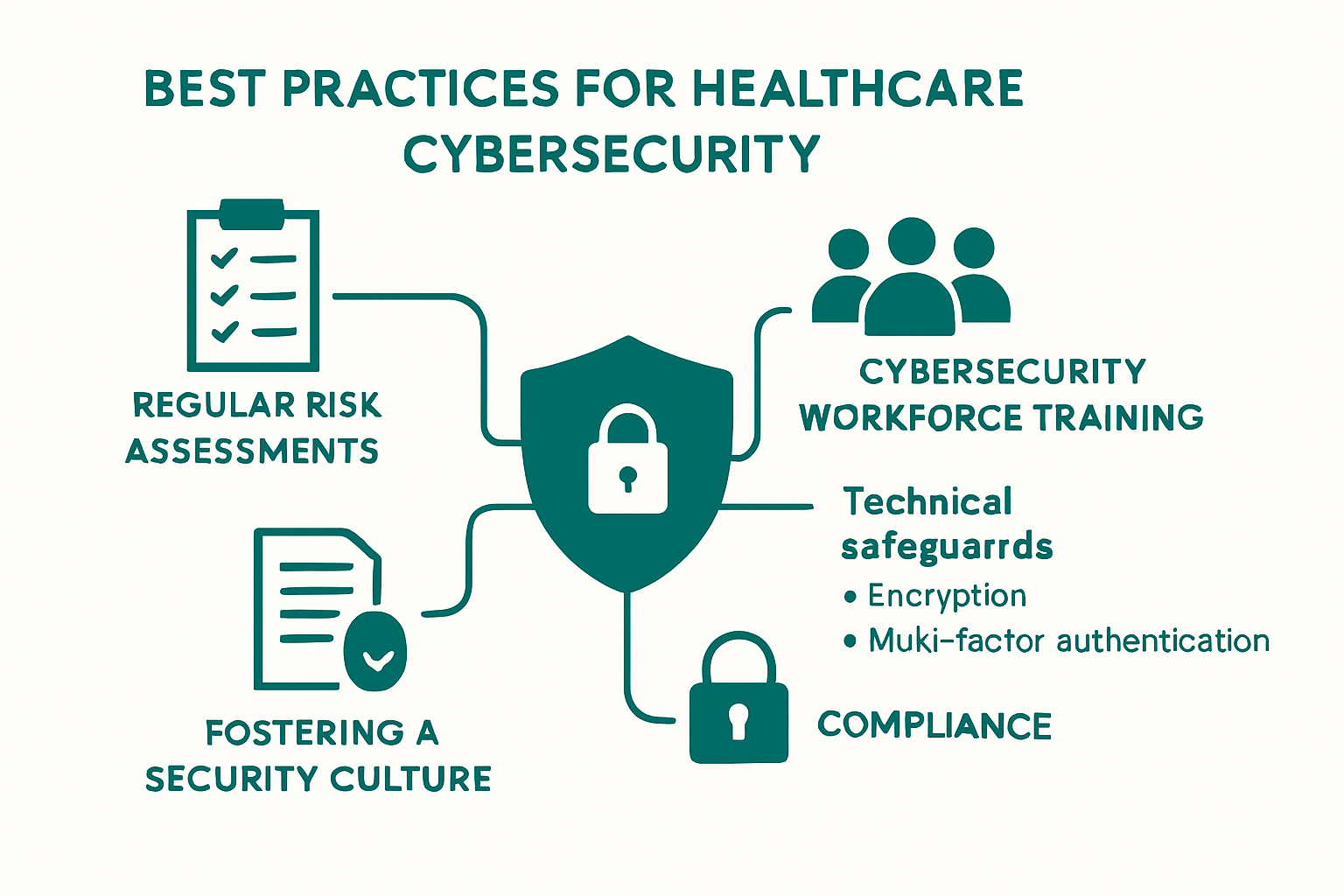
Building a Strong Security Culture in Healthcare Teams
Creating a robust cybersecurity culture within healthcare organizations requires more than technological solutions. It demands a comprehensive approach that integrates human awareness, organizational commitment, and proactive security practices across all levels of the healthcare ecosystem.
Leadership and Organizational Commitment
Effective security strategies begin at the leadership level. According to research from the National Institutes of Health, organizations with strong leadership engagement in cybersecurity demonstrate significantly lower vulnerability to potential breaches. Healthcare executives must not only allocate resources to cybersecurity initiatives but also actively model and communicate the importance of security practices.
Key leadership responsibilities include:
- Visible Security Advocacy: Consistently reinforcing the importance of cybersecurity
- Resource Allocation: Investing in training, technology, and ongoing security infrastructure
- Creating Accountability Mechanisms: Establishing clear expectations and consequences for security protocols
Comprehensive Training and Awareness Programs
Workforce education is the cornerstone of a strong security culture. Healthcare teams must receive continuous, engaging training that goes beyond generic compliance modules. This training should be practical, scenario-based, and tailored to the specific risks faced by healthcare professionals.
Effective training programs should incorporate:
- Interactive Simulation Exercises: Realistic phishing and social engineering scenarios
- Role-Specific Security Protocols: Customized guidance for different healthcare roles
- Regular Skill Assessment: Ongoing evaluation of team cybersecurity knowledge
Continuous Improvement and Adaptive Security
A dynamic security culture requires constant evolution. Healthcare organizations must develop mechanisms for continuous learning, feedback, and adaptation. This involves creating safe reporting environments where team members can discuss potential vulnerabilities without fear of punishment.
Strategies for maintaining an adaptive security approach include:
- Incident Review Processes: Transparent analysis of security events
- Open Communication Channels: Encouraging team members to report potential risks
- Regular Security Audits: Systematic evaluation of existing security practices
Building a strong security culture is not a one-time effort but an ongoing commitment. By integrating technological solutions with human awareness, healthcare organizations can create a resilient defense against evolving cyber threats. The goal is to transform security from a compliance requirement to a fundamental aspect of patient care and organizational integrity.

Meeting Compliance and Legal Requirements in Healthcare
Healthcare organizations must navigate a complex landscape of regulatory requirements that mandate robust cybersecurity practices to protect patient data and maintain operational integrity. Compliance is not merely a legal obligation but a critical component of patient trust and organizational risk management.
HIPAA Security Rule and Regulatory Framework
Navigating compliance challenges requires a comprehensive understanding of existing regulatory standards. The U.S. Department of Health and Human Services provides extensive guidance for healthcare providers to comply with the HIPAA Security Rule, which establishes national standards for protecting electronic protected health information (ePHI).
Key compliance requirements include:
The table below organizes major compliance requirements for healthcare organizations discussed in the article, highlighting their focus areas and examples for clarity.
| Compliance Requirement | Focus Area | Example(s) |
|---|---|---|
| Administrative Safeguards | Information security policies | Risk assessments, security procedures |
| Physical Safeguards | Facility and equipment protection | Securing physical infrastructure |
| Technical Safeguards | Electronic information access | Access controls, data encryption |
| Documentation and Reporting | Tracking security and compliance | Incident response plans, logs |
| Sector-Specific Compliance | Specialized regulations | NIST CMMC, international data standards |
- Administrative Safeguards: Implementing policies and procedures to manage information security
- Physical Safeguards: Protecting physical infrastructure and electronic systems
- Technical Safeguards: Controlling access to electronic patient information
Comprehensive Compliance Documentation and Reporting
According to the National Institute of Standards and Technology, healthcare organizations must develop robust documentation and reporting mechanisms to demonstrate ongoing compliance. This involves creating and maintaining detailed records of cybersecurity practices, risk assessments, and incident response protocols.
Critical documentation components include:
- Risk Management Documentation: Comprehensive logs of identified vulnerabilities and mitigation strategies
- Incident Response Plans: Detailed protocols for addressing potential security breaches
- Continuous Improvement Tracking: Evidence of ongoing security assessments and updates
Industry-Specific Compliance Considerations
Healthcare providers must also consider specialized compliance requirements beyond standard regulations. The NIST Cybersecurity Maturity Model Certification provides additional guidance for organizations working within specific sectors, such as those involved in defense-related healthcare services.
Specialized compliance considerations include:
- Sector-Specific Regulations: Understanding unique requirements for different healthcare domains
- Supply Chain Security: Ensuring compliance across interconnected healthcare networks
- International Data Protection Standards: Addressing cross-border data protection requirements
Meeting compliance and legal requirements is an ongoing process that demands continuous attention, adaptation, and proactive management. Healthcare organizations must view compliance not as a static checklist but as a dynamic approach to protecting patient data, maintaining organizational integrity, and building trust in an increasingly complex digital healthcare ecosystem.
Frequently Asked Questions
What are the top cybersecurity best practices for healthcare providers?
Implementing comprehensive risk assessments, investing in workforce cybersecurity education, and employing advanced technical safeguards like multi-factor authentication and encryption are crucial best practices for healthcare providers.
How can healthcare organizations assess their cybersecurity risks effectively?
Healthcare organizations should conduct regular vulnerability assessments, perform network architecture reviews, and map data flow to identify potential weaknesses in their systems and processes.
Why is workforce cybersecurity education important in healthcare?
Educating healthcare staff about cybersecurity reduces human errors, enhances awareness of potential threats like phishing, and equips them with the knowledge to follow protocols that safeguard sensitive patient information.
What compliance requirements should healthcare providers be aware of?
Healthcare providers must adhere to the HIPAA Security Rule, which includes administrative, physical, and technical safeguards to protect electronic protected health information (ePHI). They should also maintain comprehensive compliance documentation and be aware of sector-specific regulations.
Strengthen Patient Care with Secure and Streamlined Logistics
You have just learned how today’s healthcare cybersecurity challenges go beyond technology. Protecting patient data and meeting compliance requirements can overwhelm your team, especially when human error and complex workflows make operations even more vulnerable. As the article explored, technical safeguards and a strong culture of security are essential, but real change happens when your entire healthcare operation is synchronized and secure.
Ready to move your patient care logistics into a new era of safety and efficiency? VectorCare helps you simplify provider and vendor management, secure communication, and automated scheduling into a single platform. Discover how you can protect patient data, streamline operations, and make compliance second nature with VectorCare’s all-in-one solution. Visit our website now and see how easy it is to build workflows that put patient privacy and operational excellence at the center of your healthcare ecosystem.



